-
Xiangyu Xu, Jiadi Yu, Yingying Chen, Qin Hua, Yanmin Zhu, Yi-Chao Chen, Minglu Li,
TouchPass: Towards Behavior-irrelevant on-touch User Authentication on Smartphones Leveraging Vibrations,
in Proceedings of the 26th Annual International Conference on Mobile Computing and Networking (ACM MobiCom 2020),
London, UK, September 2020. (Acceptance rate: 24/139=17.3%)
-
Zhenzhe Lin, Yucheng Xie, Xiaonan Guo, Chen Wang, Yanzhi Ren, Yingying Chen,
WiFi-enabled Automatic Eating Moment Monitoring Using Smartphones,
in Proceedings of the 6th EAI International Conference on IoT Technologies for HealthCare (HealthyIoT 2019),
Braga, Portugal, December 2019.
- Best Paper Award
-
Li Lu, Jiadi Yu, Yingying Chen, Hongbo Liu, Yanmin Zhu, Linghe Kong, Minglu Li,
Lip Reading-based User Authentication through Acoustic Sensing on Smartphones,
IEEE/ACM Transactions on Networking (IEEE/ACM ToN), Volume 27, Issue 1, Pages 447 - 460, 2019.
-
Hao Kong, Li Lu, Jiadi Yu, Yingying Chen, Linghe Kong, Minglu Li,
FingerPass: Finger Gesture-based Continuous User Authentication for Smart Homes Using Commodity WiFi,
in Proceedings of the 20th International Symposium on Mobile Ad Hoc Networking and Computing (ACM MobiHoc 2019),
Catania, Italy, July 2019. (Acceptance rate: 37/156 = 23.7%)
-
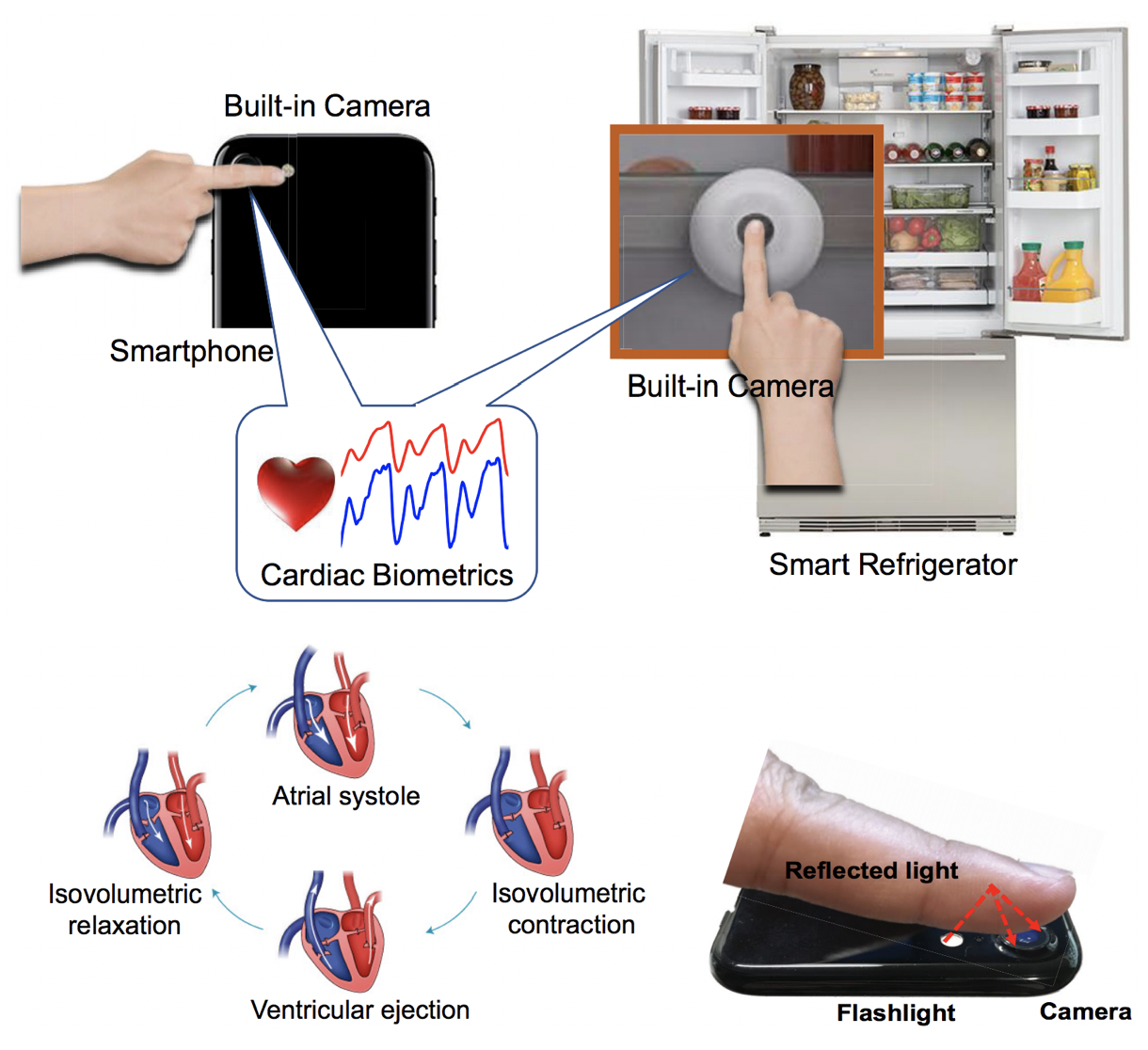
Jian Liu, Cong Shi, Yingying Chen, Hongbo Liu, Marco Gruteser,
CardioCam: Leveraging Camera on Mobile Devices to Verify Users While Their Heart is Pumping,
in Proceedings of the 17th ACM International Conference on Mobile Systems, Applications, and Services (ACM MobiSys 2019),
Seoul, South Korea, June 2019. (Acceptance rate: 40/172 = 23.2%)
-
Xiangyu Xu, Jiadi Yu, Yingying Chen, Yanmin Zhu, Linghe Kong, Minglu Li,
BreathListener: Fine-grained Breathing Monitoring in Driving Environments Utilizing Acoustic Signals,
in Proceedings of the 17th ACM International Conference on Mobile Systems, Applications, and Services (ACM MobiSys 2019),
Seoul, South Korea, June 2019. (Acceptance rate: 40/172 = 23.2%)
-
Chen Wang, Jian Liu, Yingying Chen, Hongbo Liu, Yan Wang,
Towards In-baggage Suspicious Object Detection Using Commodity WiFi, [pdf]
in Proceedings of IEEE International Communications and Network Security (IEEE CNS 2018),
Beijing, China, May/June 2018.
- Best Paper Award
- Research News:
Rutgers News,
CBS New York (WCBS TV Video),
BBC News,
NBC New York,
and Engineering 360.
-
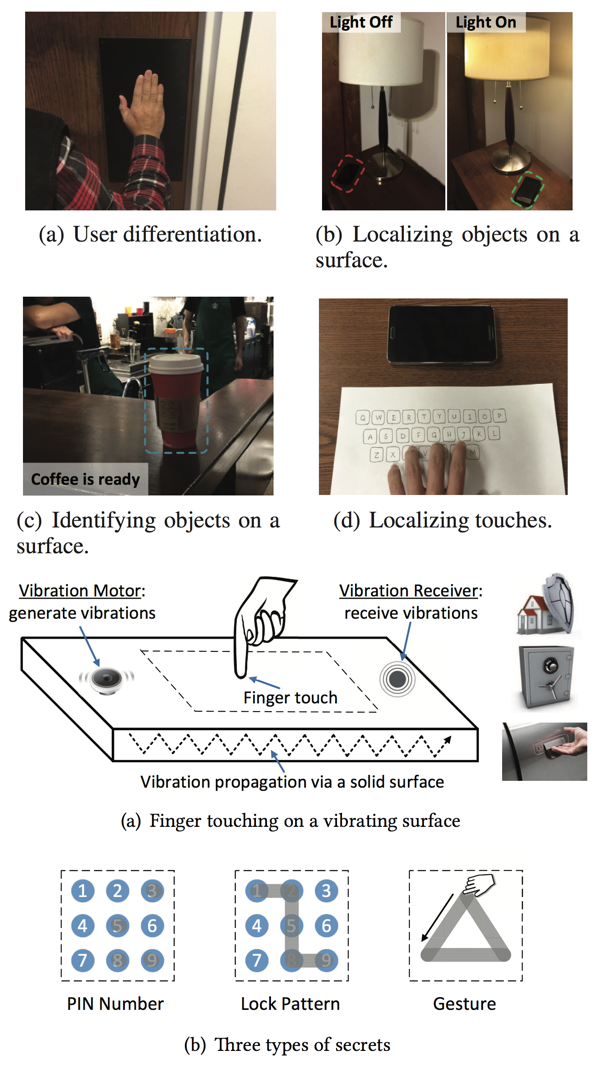
Jian Liu, Chen Wang, Yingying Chen, Nitesh Saxena,
VibWrite: Towards Finger-input Authentication on Ubiquitous Surfaces via Physical Vibration, [pdf]
in Proceedings of the 24th ACM Conference on Computer and Communications Security (ACM CCS 2017),
Dallas, USA, October-November 2017. (Acceptance rate: 151/843 = 17.9%)
- Research News:
Rutgers News,
IEEE Spectrum,
Yahoo Finance News,
NSF Science 360 News,
and Futurity.
- Here are the
presentation slides.
-
Cong Shi, Jian Liu, Hongbo Liu, Yingying Chen,
Smart User Authentication through Actuation of Daily Activities Leveraging WiFi-enabled IoT,
in Proceedings of the 18th ACM International Symposium on Mobile Ad Hoc Networking and Computing (ACM MobiHoc 2017),
Chennai, India, July 2017. (Acceptance rate: 30/179 = 16.8%)
-
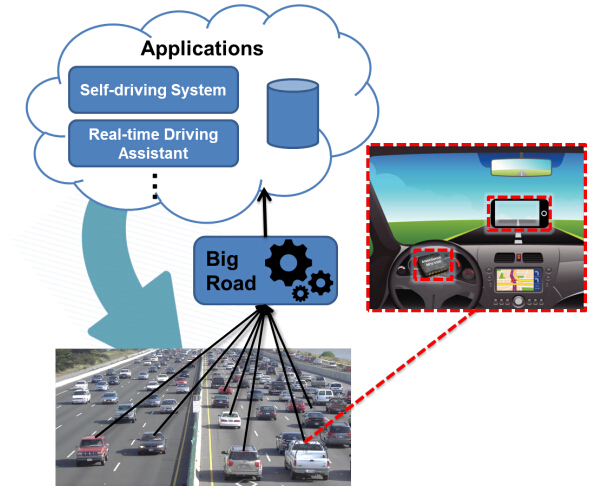
Luyang Liu, Hongyu Li, Jian Liu, Cagdas Karatas, Yan Wang, Marco Gruteser, Yingying Chen, Richard Martin,
BigRoad: Scaling Massive Road Data Acquisition for Dependable Self-Driving, [pdf], [Video Demo]
in Proceedings of the 15th ACM International Conference on Mobile Systems, Applications, and Services (ACM MobiSys 2017),
Niagara Falls, NY, USA, June 2017. (Acceptance rate: 34/191 = 17.8%)
-
Jian Liu, Yingying Chen, Marco Gruteser, Yan Wang,
VibSense: Sensing Touches on Ubiquitous Surfaces through Vibration, [pdf]
in Proceedings of the 14th IEEE International Conference on Sensing, Communication and Networking (IEEE SECON 2017),
San Diego, CA, USA, June 2017. (Acceptance rate: 45/170 = 26.5%)
- Best Paper Award
-
Chen Wang, Xiaonan Guo, Yan Wang, Yingying Chen, Bo Liu,
Friend or Foe? Your Wearable Devices Reveal Your Personal PIN, [pdf], [Presentation Slides]
in Proceedings of the 11th ACM Symposium on Information, Computer and Communications Security (ACM ASIACCS 2016),
Xi'an, China, May 2016. (Acceptance rate: 20.9%)
- Best Paper Award
- Prof. Yingying Chen is the lead researcher and the corresponding author of this paper.
- Research News:
Stevens News Release,
FORTUNE,
PHYS,
IEEE Spectrum,
and live interview with Top of Mind with Julie Rose on BYU Radio.
-
Tao Shu, Yingying Chen, Jie Yang,
Protecting Multi-Lateral Localization Privacy in Pervasive Environments, [pdf],
[BibTex],
[Google Scholar]
IEEE/ACM Transactions on Networking (IEEE/ACM ToN), Volume 23, Issue 24, Pages 1688-1701, 2015.
-
Jian Liu, Yan Wang, Gorkem Kar, Yingying Chen, Jie Yang, Marco Gruteser,
Snooping Keystrokes with mmlevel Audio Ranging on a Single Phone, [pdf], [BibTex], [Google Scholar],
[Video Demo]
in Proceedings of the 21st Annual International Conference on Mobile Computing and Networking (ACM MobiCom 2015),
Paris, France, September 2015. (Acceptance rate: 38/207 = 18.4%)
-
Shubham Jain, Carlo Borgiattino, Yanzhi Ren, Marco Gruteser,
Yingying Chen, Carla-Fabiana Chiasserini,
LookUp: Enabling Pedestrian Safety Services via Shoe Sensing, [pdf], [BibTex],
[Google Scholar], [Video
Demo]
in Proceedings of the 13th International Conference on Mobile Systems,
Applications, and Services (ACM MobiSys 2015),
Florence, Italy, May 2015. (Acceptance rate: 29/219 = 12%)
-
Jian Liu, Yan Wang, Yingying Chen, Jie Yang, Xu Chen, Jerry Cheng,
Tracking Vital Signs During Sleep Leveraging Off-the-shelf WiFi, [pdf], [BibTex],
[Google Scholar], [Video
Demo]
in Proceedings of the 16th ACM Symposium on Mobile Ad Hoc Networking and Computing (ACM MobiHoc 2015),
Hangzhou, China, June 2015. (Acceptance rate: 14.8%)
- Research News:
MIT Technology Review,
Fierce Mobile Healthcare,
Digital Journal,
Yahoo News,
Mobile Health Clinic,
Stevens News,
Zeenews,
MIT 科技评论,
网易科技, and
电子工程世界.
-
Yanzhi Ren, Chen Wang, Jie Yang, Yingying Chen,
Fine-grained Sleep Monitoring: Hearing Your Breathing with Smartphones, [pdf], [BibTex],
[Google Scholar], [Video Demo]
in Proceedings of the IEEE International Conference on Computer Communications (IEEE INFOCOM 2015),
Hong Kong, China, April 2015. (Acceptance rate: 316/1640 = 19.3%)
- Research News:
MIT Technology Review,
Fierce Mobile Healthcare,
Digital Journal,
Yahoo News,
Mobile Health Clinic,
Stevens News,
Zeenews,
MIT 科技评论,
网易科技, and
电子工程世界.
-
Jiadi Yu, Jiaming Zhao, Yingying Chen, Jie Yang,
Sensing Ambient Light for User Experience-Oriented Color Scheme Adaptation on Smartphone Displays, [pdf], [BibTex],
[Google Scholar]
in Proceedings of the The 13th ACM Conference on Embedded Networked Sensor (ACM SenSys 2015),
Seoul, South Korea, November 2015. (Acceptance rate: 27/132 = 20.5%)
-
Jie Yang, Yingying Chen,
Wade Trappe, and Jerry Cheng, Pervasive Wireless Environments: Detecting and Localizing User Spoofing,
ISBN: 978-3-319-07355-2,Springer, 2014.
-
Yan Wang, Jian Liu, Yingying Chen, Marco Gruteser, Jie Yang, Hongbo Liu,
E-eyes: Device-free Location-oriented Activity Identification Using Fine-grained WiFi Signatures,
[pdf], [BibTex],
[Google Scholar]
in Proceedings of the 20th Annual International Conference on Mobile Computing and Networking (ACM MobiCom 2014),
Maui, Hawii, Sept. 2014. (Acceptance rate: 36/220 = 16.4%)
-
Gorkem Kar, Hossen Mustafa, Yan Wang, Yingying Chen, Wenyuan Xu, Marco Gruteser, Tam Vu,
Detection of On-Road Vehicles Emanating GPS Interference, [pdf], [BibTex],
[Google Scholar]
in Proceedings of the ACM Conference on Computer and Communications Security (ACM CCS 2014),
Scottsdale, Arizona, Nov. 2014. (Acceptance rate: 114/585 = 19.5%)
-
Xiuyuan Zheng, Chen Wang, Yingying Chen, Jie Yang,
Accurate Rogue Access Point Localization Leveraging Fine-grained Channel Information,
[pdf], [BibTex],
[Google Scholar]
in
Proceedings of the IEEE Conference on Communications and Network Security
(IEEE CNS 2014),
San Fransisco, CA, Oct. 2014.
- Best Paper Award
-
Hongbo Liu, Yingying Chen, Mooi Choo Chuah, Jie Yang,
Towards Self-Healing Smart Grid via Intelligent Local Controller Switching under Jamming,
[pdf], [BibTex],
[Google Scholar]
in
Proceedings of IEEE Conference on Communications and Network Security
(IEEE CNS 2013),
Washington, D.C., USA, October 2013.
- Best Paper Runner-Up.
-
Hongbo Liu, Yu Gan, Jie Yang, Simon Sidhom, Yan
Wang, Yingying Chen, Fan Ye,
Push the Limit of WiFi based Localization for Smartphones,
[pdf], [BibTex],
[Google Scholar]
in Proceedings of the 18th Annual International Conference on Mobile Computing
and Networking (ACM MobiCom 2012),
Istanbul, Turkey, August 2012.
(Acceptance rate: 32/212 = 15%)
- Here are the
presentation slides and
demo.
-
Jie Yang, Simon Sidhom, Gayathri
Chandrasekaran, Tam Vu, Hongbo Liu, Nicolae Cecan, Yingying Chen, Marco
Gruteser, Richard P. Martin,
Detecting Driver Phone Use Leveraging Car Speakers,
[pdf], [BibTex],
[Google Scholar]
in Proceedings of the 17th Annual International Conference on Mobile
Computing and Networking (ACM MobiCom 2011),
Las Vegas, Nevada, USA, September 2011. (Acceptance rate: 13.5%)
- Best
Paper Award. Here are the
presentation slides.
- Research News:
The Wall Street Journal,
MIT Technology Review,
Fox News Channel,
Inside Science TV,
New Jersey My9,
VOA-TV,
Tonight Show with Jay Leno,
CNet,
Yahoo News,
WCBS,
CSDN,
Sohu and Sina.
-
Yingying Chen, Wenyuan Xu, Wade Trappe, Yanyong Zhang,
Securing Emerging Wireless Systems,
ISBN:978-0-387-88490-5,Springer, 2009.
-
Yingying Chen, Wade Trappe, Richard P.
Martin,
Detecting and Localizing Wireless Spoofing Attacks,
[pdf],
[BibTex], [Google
Scholar]
in Proceedings of the Fourth Annual IEEE
Communications Society Conference on Sensor, Mesh and Ad Hoc Communications
and Networks (IEEE SECON 2007),
San Diego, CA, USA, May 2007.(Acceptance rate: 20%)
-
Yingying Chen,
John-Austin Francisco, Wade Trappe, Richard P. Martin,
A Practical Approach to Landmark Deployment for Indoor Localization, [pdf],
[BibTex], [Google
Scholar]
in Proceedings of the Third Annual IEEE Communications Society
Conference on Sensor, Mesh and Ad Hoc Communications and Networks
(IEEE
SECON 2006),
Reston, VA, USA, September 2006.(Acceptance rate: 26%)

.jpg)

.jpg)

.jpg)
.jpg)