| |
Utilizing Contextual Channel Characteristics for Secure Communications in Wireless Ad Hoc Networks |
|
|
|
|
Bootstrapping security among devices is a crucial step for deploying wireless ad hoc networks in sensitive and mission-critical applications. Most existing solutions to security bootstrapping assume the existence of common resources such as additional hardware, auxiliary secure out-of-band (OOB) channels, or pre-existed trust among devices. In pervasive environments, however, these assumptions are not always practical. Given the tremendous number of wireless devices available nowadays, devices can be heterogeneous and highly diversified in hardware capabilities or user interfaces, and have limited common resources. Our research conducts an exploratory study on bootstrapping security in wireless ad hoc networks based on wireless channel characteristics under various real-world contexts, without assuming additional hardware, OOB channel or pre-existed trust with wireless devices. Specifically, the emphasis of the research is on the following issues: |
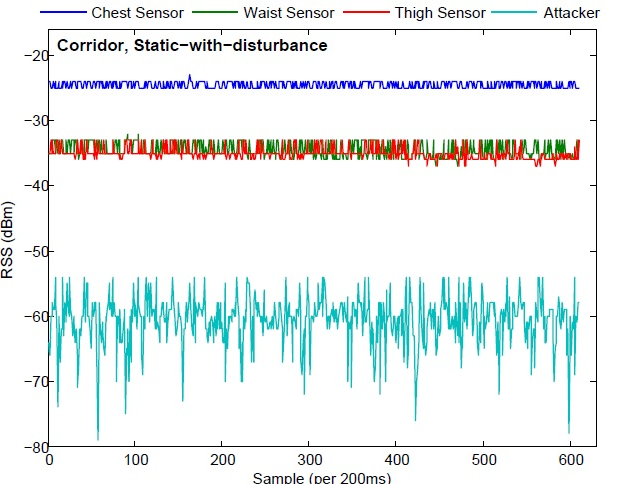
Study of contextual channel characteristics in representative ad hoc networks. Due to the complexity of radio signal propagation, wireless communication channels are frequently subject to multi-path fading and interferences, and are sensitive to the surrounding environments. Although such dynamics of wireless channels introduce challenges to the efficiency and robustness of communications, they also provide unique sources ideal for bootstrapping security for communications due to the randomness and reciprocitiy properties of wireless channels under certain contexts [1]. To understand wireless channel properties under various real-world scenarios as well as their applicability to security bootstrapping, this work carries out extensive experiments under different types of ad hoc networks including body area networks and vehicular networks. Contextual factors such as indoor/outdoor locations, platform movements, interference from nearby environments and the type wireless radio are considered in the experiments [2]. |
 |
|
Security bootstrapping exploiting contextual channel characteristics. Based on the contextual wireless characteristics, this work conducts preliminary research to explore the feasibility of bootstrapping wireless security in terms of device authentication, secret key generation, and the simultaneous execution of both. In order to minimize the assumption on the available hardware and out-of-band resources, this research aims to achieve the objectives based received signal strength (RSS) which can be conveniently available to most commodity wireless devices. Various powerful attacks such as man-in-the-middle (MITM) attacks are to be addressed in the research. Efficiency in terms of secret key generation rate is also studied in this work. Promising techniques such as collaborative security bootstrapping for simultaneous secret key generation and device athentication [3] are proposed and investigated.
Testbed and validation. This research implements testbed with a variety of commodity devices such as laptops, wireless sensors and smartphones to simulate real-world scenarios including body area networks and vehicular networks. The validation of the work considers various factors such as location and mobility of wireless devices.
|
|
|
| Related Publications |
- Yantian Hou, Ming Li, and Shucheng Yu, "Surviving the RF Smog: Making Body Area Networks Robust to Cross-Technology Interference", accepted, IEEE Transactions on Wireless Communications, 2016.
- Lu Shi, Ming Li, Shucheng Yu, and Jiawei Yuan, "BANA: Body Area Network Authentication Exploiting Channel Characteristics", IEEE Journal on Selected Areas in Communications (JSAC), vol.31, issue 9, pp. 1803-1816, September, 2013.
- Lu Shi, Jiawei Yuan, Shucheng Yu, and Ming Li, "MASK-BAN: Movement-Aided Authenticated Secret Key Extraction Utilizing Channel Characteristics in Body Area Networks", IEEE Internet of Things Journal, vol.2, no.1, pp:52-62, February, 2015.
|
|
| |
|
|
| Acknowledgement: We thank the generous support by NSF grant CNS-1347552. |  |
|
|
All Rights Reserved. 2015 |
| |

