SaTC: CORE: Small: Toward Usable and Ubiquitous Trust Initialization and Secure Networking in Wireless Ad Hoc Networks |
| Principle Investigator: Dr. Shucheng Yu |
Understanding Wireless Channels To boostrap security and protect wireless devices with limited or no cryptographic capabilities, one approach is to utilize the intrinsic properties and/or randomnesses of wireless channels or hardware fingerprints as the source of security. In the literature, a rich set of wireless characteristics have been used including multipath signatures, hardware fingerprints and other contextual information. To extract these characteristics with minimal user engagement, one way is to analyze the channel state information (CSI) which is measurable at the receiver during wireless communications. Previous research has discovered that the CSI measurements at the receiver are usually mixed with the following errors. Specifically, we can formulate the channel response as follows: $$\hat{H}_{t,k,s} =\hat{H}_{t,k,s} e^{-j \phi_{t,k,s}}$$ where $$\phi_{t,k,s} =\underbrace{\psi_{t,k,s}}_\text{ToF}+\underbrace{\alpha_{t,k}}_\text{STO}+\underbrace{\gamma_{t,k}}_\text{SFO}+\underbrace{\beta_t}_\text{CFO}+\underbrace{\zeta_s }_\text{CPO}+\underbrace{\epsilon}_\text{AWGN}$$ In addition to the attenuation of signal power, a rich set of information is embedded in the errors with phase shifts measurable in CSI. To be more precise, the phase shift can be caused by the propagation of RF signal in the air (i.e. Time of Flight (ToF)), the disparity of sampling frequency between TX/RX (i.e., the Sampling Frequency Offset (SFO)), the small shift in time-synchronization between sender and receiver which causes Symbol Time Offset (STO), the TX-RX carrier frequency offset (CFO), and the mismatch between TX and RX in initial carrier phase which is termed as carrier phase offset (CPO), in addition the Gaussian noise. In this project, we conducted an extensive survey [1] on the types of wireless characteristics which are considered as errors in other research such as wireless localization but can be potentially utilized as sources for fingerprinting in wireless security (e.g., for authentication and secret key extraction).
Device Fingerprinting with Hardware Errors Measurable in CSI Device identification is a critical initial step for security bootstrapping of wireless devices which do not hold prior trust. Without using cryptographic credentials, we resort to unique hardware characteristics for device fingerprinting. Along this direction, previous research has considered sources such as IQ offset and SYNC correlation [2], imperfections of Digital-to-analog converter (DAC) and the power amplifiers (PA) [3]. This line of work usually require a custom hardware (e.g., VNA, USRP) to measure the hardware characteristics. Athough effective, this approach exhibit low usability in real-world deployment considering limited resources or expertise available at users. Toward measure the hardware characteristics wirelessly without the help of custom hardware, a recent research [4] considered unique carrier phase offsets (CPO) of TX devices as the source for fingerprinting. The idea of [4] is based on the linearity of measured CPO versus time. To extract the CPO, it assumes static channel during measurements which usually last for miniutes. While this approach is shown effective in static scenarios, it is vulnerable to environment changes and cannot support mobile devices. In this project, we turns to utilize mismatch of the random initial phase offsets between TX/RX, which is primarily contributed by CPO, as the source for device fingerprinting. One benefit of using CPO is that it is not time or frequent variant. Therefore, it serves as a more reliable but unique characteristics (each hardware has its own radom initial phase offsets) which can be measured under devices mobility or environmental changes. To evaluate our approach, we conducted extensive experiments [5] in indoor environments which subject to rich multipath effects.
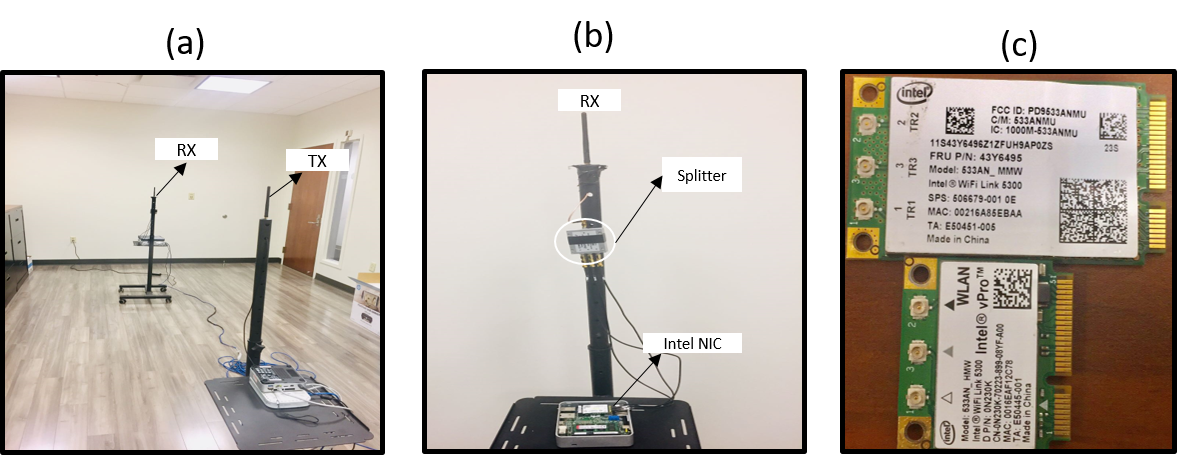
During the experiments, we tested 17 Intel 5300 NIC cards (9 full mini-PCIe cards and 8 half mini-PCIe cards). For each card, we transmitted 100,000 packets and used spatial multiplexing (injection code of 0x1c911) to extract the relative phase between the TX antennas. Mean, variance, skewness, kurtosis of measurements of each antenna are used to build a neural network model and make predictions. We used 85,000 samples for training a model and 15,000 for prediction. The raw measurements can be visualized in Figure 3 (left). When transmitter and receiver are not moving, we obtain accuracy of 93-97 % while distinguishing among 17 MIMO transceivers in different indoor settings.
Next Steps Based on the initial results of device fingerprinting, this project will continue to investigate secure device authentication using comprehensive information including device fingerprints and contextual information introduced by devices dynamics (e.g., mobility) and research on optimal strategies for secure wireless communication protection using friendly jamming.